OPC UA™
OPC Unified Architecture (OPC UA) protocol for secure industrial data access in read-only mode, supporting both Historical Access (HA) and Data Access (DA) modes.
- Modern successor to OPC Classic™ (see OPC Classic™ connector)
- TCP/IP based with tree-like address space
- Uses node IDs for data referencing
- Implemented using node-opcua library
- Natively embedded in many industrial controllers
Specific Settings
Connection Configuration
| Setting | Description |
|---|---|
| Endpoint URL | URL of the OPC UA server (e.g., opc.tcp://localhost:4840) |
| Keep session alive | Keep session alive between messages |
| Retry Interval | Delay between retries (in milliseconds) |
| Read timeout | Maximum execution time (ms) for requests |
Data Throttling
| Setting | Description | Example Value |
|---|---|---|
| Number of messages before flush | Number of messages to accumulate before flushing to North caches | 1000 |
| Delay between flush | Time delay (in milliseconds) between automatic flushes of accumulated messages | 1000 |
Security Settings
| Setting | Description |
|---|---|
| Security Mode | Security mode for the connection (None, Sign, SignAndEncrypt) |
| Security Policy | Security policy for the connection (None, Basic128Rsa15, Basic256, etc.) |
Authentication Methods
| Method | Description | Required Parameters |
|---|---|---|
| Anonymous | Connect without authentication. | None |
| Username/Password | Standard username/password authentication. | Username, Password |
| Certificate | Authentication using client certificates. | Client Certificate, Private Key |
Throttling Settings
You can optimize data requests using throttling configurations. These settings help manage large data intervals and network conditions effectively.
Key Throttling Parameters
| Setting | Description | Data Type | Example Value |
|---|---|---|---|
| Max read interval | Maximum duration (in seconds) for each data request interval. Larger intervals are automatically divided into smaller chunks not exceeding this value. | Seconds | 3600 |
| Read delay | Delay (in milliseconds) between consecutive data requests. Helps prevent server overload. | Milliseconds | 1000 |
| Overlap | Time overlap (in milliseconds) between consecutive queries to ensure data continuity. This value is subtracted from the @StartTime of the next query. | Milliseconds | 60000 |
How Throttling Works
- Interval Division:
- Large time ranges are automatically split into smaller intervals
- Each sub-interval does not exceed the
Max read intervalduration - Example: A 24-hour request with
Max read interval = 3600(1 hour) will be split into 24 separate 1-hour requests
- Request Timing:
- The
Read delayintroduces a pause between consecutive requests - Helps manage server load and prevents rate limiting
- Particularly useful during network instability or when querying large datasets
- Data Continuity:
- The
Overlapsetting ensures no gaps in your data - Creates a time buffer between consecutive queries
- Example: With
Overlap = 60000(1 minute), each query will include 1 minute of overlapping data with the previous query
The overlap setting modifies the @StartTime of each query by subtracting the overlap value from the calculated start time. This adjustment applies to the entire query range, not to individual sub-intervals when large requests are split into smaller chunks.
This functionality is particularly useful when:
- New data is ingested after previous queries have executed
- You need to account for potential ingestion delays in the source system
Example:
With overlap=60000 (1 minute), a query for the interval [10:00-11:00] will actually request [9:59-11:00], ensuring capture of any late-arriving data from the previous time period.
Recommended Configurations
| Scenario | Max read interval | Read delay | Overlap |
|---|---|---|---|
| Stable network, small datasets | 3600 (1 hour) | 500 | 0 (no overlap) |
| Unstable network | 1800 (30 min) | 2000 | 0 (no overlap) |
| Large historical retrievals | 7200 (2 hours) | 1000 | 0 (no overlap) |
| Real-time with occasional gaps | 900 (15 min) | 200 | 15000 (15 sec) |
Item Settings
| Setting | Description | HA Mode Options | DA Mode Options |
|---|---|---|---|
| Node ID | Data path in server namespace | ns=3;i=1001 or ns=3;s=Counter | Same as HA |
| Mode | Data access method | HA or DA | - |
| Aggregate | Value aggregation (HA only) | Raw, Average, Min, Max | N/A |
| Resampling | Interval resampling (HA only) | None, 1s, 5m, 1h | N/A |
- Verify server supports selected mode (HA/DA)
- Not all servers support all aggregation/resampling options
- Recommended: Use
Rawaggregation andNoneresampling
Security Configuration
Communication Security
- OIBus generates self-signed certificate on startup
- Certificate location:
<south_cache>/opcua/ - Must be trusted by OPC UA server
- Error if untrusted:
The connection may have been rejected by the server
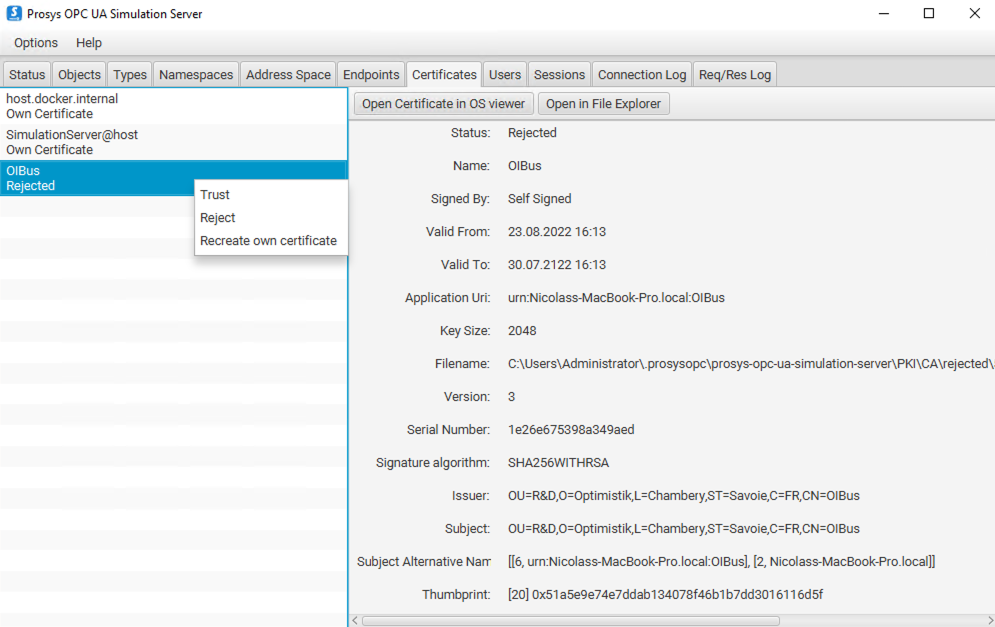
Certificate Management
- Communication Certificate:
- Auto-generated by OIBus
- Location:
<south_cache>/opcua/cert.pem
- Authentication Certificate:
- Must be added to server's trusted certificates
- Prosys location:
.prosysopc\prosys-opc-ua-simulation-server\USERS_PKI\CA\certs - Error if rejected:
BadIdentityTokenRejected (0x80210000)
Move rejected certificates from:
.prosysopc\prosys-opc-ua-simulation-server\USERS_PKI\CA\rejected
to:
.prosysopc\prosys-opc-ua-simulation-server\USERS_PKI\CA\certs
Certificate Creation for Prosys
- Create
cert.conf:
[ req ]
default_bits = 2048
default_md = sha256
distinguished_name = subject
req_extensions = req_ext
x509_extensions = req_ext
string_mask = utf8only
prompt = no
[ req_ext ]
basicConstraints = CA:FALSE
nsCertType = client, server
keyUsage = nonRepudiation, digitalSignature, keyEncipherment, dataEncipherment, keyCertSign
extendedKeyUsage= serverAuth, clientAuth
nsComment = "OIBus User Cert"
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
subjectAltName = URI:urn:opcua:user:oibus,IP: 127.0.0.1
[ subject ]
countryName = FR
stateOrProvinceName = FR
localityName = Chambéry
organizationName = OI
commonName = oibus
- Generate certificate:
# Create key and certificate
openssl req -new -x509 -keyout oibus.key -out oibus.pem -config cert.conf
# Remove passphrase
openssl rsa -in oibus.key -out oibus.key
# Convert to DER format
openssl x509 -inform PEM -outform DER -in oibus.pem -out oibus.der
- Install in Prosys:
cp oibus.der .prosysopc/prosys-opc-ua-simulation-server/USERS_PKI/CA/certs/
The same certificate can be used for:
- Secure communication (sign/encrypt)
- Client authentication: Specify paths to
cert.pemandprivate.pem